Why Defense Contractors Need to Understand CMMC Now
CMMC (Cybersecurity Maturity Model Certification) is a Department of Defense program that verifies defense contractors meet specific cybersecurity standards before they can bid on or maintain contracts involving Federal Contract Information (FCI) or Controlled Unclassified Information (CUI).
Quick Overview:
- Purpose: Protect sensitive information in the $768 billion Defense Industrial Base supply chain
- Three Levels: Foundational (Level 1), Advanced (Level 2), and Expert (Level 3)
- Assessment Types: Self-assessments, third-party certifications (C3PAO), and government-led audits (DIBCAC)
- Timeline: Final rule published September 10, 2025, with phased implementation through contracts
- Impact: Mandatory requirement for DoD contractors and subcontractors handling FCI or CUI
If your business serves the Defense Industrial Base—even as a subcontractor—CMMC 2.0 isn’t optional. It’s a contractual requirement that determines whether you can compete for and win government work.
The program streamlines the original five-level framework into three tiers, aligning requirements with established NIST cybersecurity standards like SP 800-171 and SP 800-172. Unlike the previous self-attestation approach under DFARS 252.204-7012, CMMC 2.0 requires verified compliance through formal assessments.
This represents a fundamental shift in how the DoD ensures cybersecurity across its supply chain. The stakes are significant: CMMC impacts an industry worth 3.2% of the entire U.S. Gross Domestic Product.
I’m Jay Baruffa, and over my 20+ years designing IT systems and infrastructure, I’ve helped Northeast Ohio businesses steer complex compliance requirements including CMMC readiness assessments and security frameworks. At Tech Dynamix, we work with contractors who need practical guidance through these evolving cybersecurity mandates without the technical overwhelm.
The Evolution and Purpose of the CMMC Program

The Cybersecurity Maturity Model Certification (CMMC) program, particularly its 2.0 iteration, represents a critical step forward in safeguarding sensitive information within the Defense Industrial Base (DIB). The DIB is a massive sector, impacting the $768 billion defense industry, which accounts for a substantial 3.2% of the U.S. Gross Domestic Product. Our goal is to ensure that this vital economic engine, and the national security it underpins, remains resilient against changing cyber threats.
The primary purpose of CMMC 2.0 is to provide the Department of Defense (DoD) with a robust and transparent mechanism to verify that contractors and subcontractors handling sensitive government information have implemented adequate cybersecurity protections. This isn’t just a suggestion; it’s a contractual requirement. If your business in Northeast Ohio, from Painesville to Hudson, handles Federal Contract Information (FCI) or Controlled Unclassified Information (CUI) for the DoD, achieving a specific CMMC level will be a prerequisite for contract award.
The journey to CMMC 2.0 has been a long one, rooted in decades of cybersecurity efforts. It builds upon foundational legislation like the Federal Information Security Management Act (FISMA) enacted in 2002, which mandated information security programs for federal agencies. Over the years, various NIST (National Institute of Standards and Technology) publications, such as NIST SP 800-171, provided guidance for protecting CUI in non-federal systems. The DFARS (Defense Federal Acquisition Regulation Supplement) clause 252.204-7012, which went into effect in 2016, specifically required defense contractors to implement NIST SP 800-171 controls and report cyber incidents.
However, the DoD recognized a gap: self-attestation wasn’t providing sufficient assurance. This led to the introduction of CMMC 1.0, and subsequently, the more streamlined and focused CMMC 2.0. The current version refines the framework into a tiered model, making it more digestible and aligning requirements more directly with existing NIST standards. This structured approach ensures that the level of cybersecurity maturity aligns with the type and sensitivity of the information being handled.
CMMC 2.0’s key features include this tiered model, which assesses compliance at progressively advanced levels based on information sensitivity, and an assessment requirement that verifies DIB implementation of foundational cybersecurity standards. For us at Tech Dynamix, specializing in Cybersecurity Solutions for businesses across the Greater Cleveland Area, understanding this evolution is crucial. It allows us to guide our clients through the necessary steps to meet these stringent requirements, ensuring their continued eligibility for defense contracts and, most importantly, protecting critical national security information.
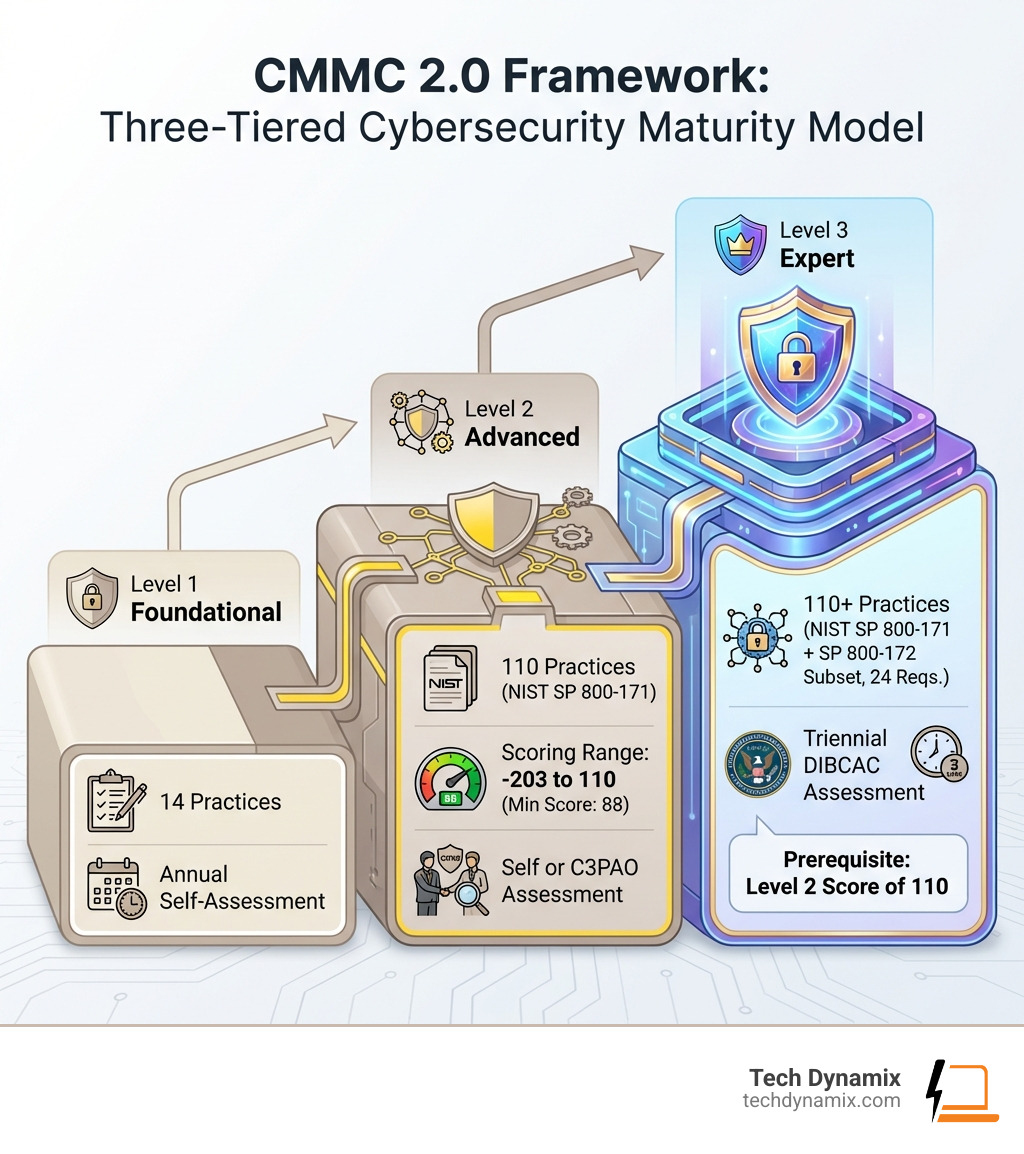
Breaking Down the Three CMMC Levels
CMMC 2.0 simplifies the previous five-level model into three distinct tiers, each designed to address varying degrees of information sensitivity and cyber risk. Understanding these levels is fundamental for any organization in our region participating in the DIB, as they dictate the specific cybersecurity practices you must implement and the assessment method required.
Here’s a breakdown of the three CMMC 2.0 levels:
| CMMC Level | Information Type Handled | Number of Practices | Basis for Practices | Assessment Type | Assessment Frequency | Scoring |
|---|---|---|---|---|---|---|
| Level 1: Foundational | Federal Contract Information (FCI) | 15 | FAR 52.204-21 | Annual Self-Assessment | Annually | MET/NOT MET |
| Level 2: Advanced | Controlled Unclassified Information (CUI) | 110 | NIST SP 800-171 Rev 2 | Annual Self-Assessment (non-critical CUI) or Triennial C3PAO Assessment (critical CUI) | Annually (self) / Every 3 Years (C3PAO) | Point-based (-203 to 110, minimum 88) |
| Level 3: Expert | CUI for highest-priority DoD programs | 110+ (NIST SP 800-171 + subset of NIST SP 800-172) | NIST SP 800-171 Rev 2 & NIST SP 800-172 | Triennial DIBCAC Assessment | Every 3 Years | Point-based (Max 24, prerequisite Level 2 score of 110) |
Level 1: Foundational
This entry-level tier is for organizations that only handle Federal Contract Information (FCI). FCI is information, not CUI, provided by or generated for the Government under a contract. If your business processes, stores, or transmits FCI, you’ll need to meet the 15 safeguarding requirements outlined in FAR clause 52.204-21. These requirements are considered “basic cyber hygiene.” For Level 1, organizations perform an annual self-assessment, which simply determines if each practice is “MET” or “NOT MET.” No complex scoring is involved, but an annual affirmation from a senior company official is required.
Level 2: Advanced
Level 2 is where the majority of DIB contractors will find themselves, as it applies to those handling Controlled Unclassified Information (CUI). This level aligns directly with the 110 security requirements specified in NIST SP 800-171 Rev 3. These practices are significantly more robust than Level 1, encompassing areas like access control, incident response, and system integrity.
The assessment approach for Level 2 is nuanced:
- For CUI that is not critical to national security, organizations can perform annual self-assessments, similar to Level 1, but with a more detailed point-based scoring system.
- For CUI that is critical to national security, a triennial (every three years) third-party assessment conducted by an accredited CMMC Third-Party Assessment Organization (C3PAO) is required.
Level 2 scoring is unique, with requirements valued at 1, 3, or 5 points, leading to a range of -203 to 110. A minimum passing score of 88 is required. Interestingly, partial credit is allowed for certain implementations, such as multi-factor authentication (MFA) and FIPS-validated cryptography, which can prevent score deductions.
Level 3: Expert
This highest level is reserved for organizations handling CUI for the DoD’s most critical and highest-priority programs. Level 3 builds upon the 110 practices of NIST SP 800-171 and adds a subset of improved security requirements from NIST SP 800-172. While the exact number of additional practices is still being finalized, it will be 110+ practices with 320+ total objectives.
Assessments for Level 3 are the most stringent. They are conducted every three years by the Defense Industrial Base Cybersecurity Assessment Center (DIBCAC), a government entity. All Level 3 security requirements are valued at 1 point, with a maximum score of 24. A critical prerequisite for Level 3 is achieving a perfect score of 110 on the Level 2 assessment, demonstrating a robust foundation of cybersecurity.
For businesses in Northeast Ohio, understanding these distinctions is vital. Whether you’re a small machine shop in Lake County or a professional services firm in Summit County, the type of information you handle will determine your CMMC level and the path you need to take for compliance.
Navigating the Assessment Ecosystem
Achieving CMMC compliance isn’t just about implementing controls; it’s also about navigating a structured assessment ecosystem designed to verify your cybersecurity posture. This ecosystem involves several key players and processes, ensuring consistency and integrity across the Defense Industrial Base.
At its core, the CMMC program defines specific roles for conducting assessments. An Organization Seeking Assessment (OSA) is simply any entity, like your business in the Greater Cleveland Area, that is undergoing a CMMC assessment.
For CMMC Level 1 and certain Level 2 scenarios (those not involving CUI critical to national security), organizations can perform annual self-assessments. These self-assessments, along with an annual affirmation from a senior company official, must be registered in the Supplier Performance Risk System (SPRS). This allows the DoD to have visibility into your stated compliance.
However, for Level 2 assessments involving critical CUI, and for all Level 3 assessments, external validation is required. This is where specialized organizations come into play:
- CMMC Third-Party Assessment Organizations (C3PAOs): These are independent entities accredited by The Cyber AB to conduct Level 2 certification assessments. If your business needs a C3PAO assessment, you’ll find accredited providers listed on The Cyber AB Marketplace. They play a crucial role in verifying your implementation of NIST SP 800-171 controls.
- The CMMC Accreditation Body (The Cyber AB): This non-governmental body is contracted by the DoD to accredit and oversee the entire CMMC ecosystem. They are responsible for accrediting C3PAOs, as well as the CMMC Assessors and Instructors Certification Organization (CAICO). Essentially, The Cyber AB ensures the quality and consistency of CMMC assessments and training.
- CMMC Assessors and Instructors Certification Organization (CAICO): CAICO, which operates under the purview of The Cyber AB, is responsible for training and certifying the individual assessors and instructors who will conduct CMMC assessments or prepare organizations for them. This ensures that the personnel performing these critical evaluations are qualified and knowledgeable.
- Defense Industrial Base Cybersecurity Assessment Center (DIBCAC): For the most stringent Level 3 assessments, the Defense Industrial Base Cybersecurity Assessment Center (DIBCAC), a government entity, takes the lead. Because Level 3 requires the highest level of security for the most sensitive CUI, DIBCAC’s involvement ensures direct government oversight and expertise in these assessments. These assessments are conducted every three years.
As your trusted IT partner in Northeast Ohio, we understand that this ecosystem can seem complex. Our Compliance & Security Audits services are designed to help you steer these waters, preparing your organization for the appropriate assessment, whether it’s a self-assessment or a full C3PAO or DIBCAC audit.
The Role of a Certified CMMC Professional (CCP)
Within the CMMC assessment ecosystem, individual expertise is paramount. This is where the Certified CMMC Professional (CCP) credential comes into play. A CCP is an individual who has demonstrated a foundational understanding of the CMMC framework, its requirements, and the assessment process.
The CCP credential is a critical stepping stone for anyone aspiring to become a CMMC Certified Assessor (CCA). It serves as a prerequisite, ensuring that all assessors possess a common baseline of knowledge before they can participate in official CMMC assessments. The CCP exam, launched in October 2022 by CAICO, validates this knowledge.
Ideal candidates for a CCP are professionals working in cybersecurity, compliance, information technology, governance, or risk roles who support—or aspire to support—defense-sector organizations. This includes consultants and advisors who guide contractors through readiness activities, documentation development, and pre-assessment preparation. For us, having CCP-certified experts on our team means we can offer our clients in Summit County and beyond the most accurate and up-to-date guidance on their CMMC journey.
Documentation and Reporting via SPRS and eMASS
Proper documentation and reporting are integral to the CMMC compliance process. The DoD relies on specific systems to track and verify the cybersecurity posture of its DIB partners.
For CMMC Level 1 and Level 2 self-assessments, organizations must submit their results to the Supplier Performance Risk System (SPRS). This submission includes the annual self-assessment against the relevant requirements (15 for Level 1, 110 for Level 2) and an annual affirmation from a senior company official. This ensures that the DoD has a record of your organization’s stated compliance and commitment.
For Level 2 C3PAO-led assessments and all Level 3 DIBCAC assessments, the process is more formal. The assessment reports, detailing findings and outcomes, are uploaded into the CMMC Enterprise Mission Assurance Support Service (eMASS). eMASS is a DoD-wide system used for managing the authorization and accreditation of information systems. This centralized repository allows the DoD to review assessment findings, track Plans of Action and Milestones (POA&M) for any identified deficiencies, and ultimately grant or deny CMMC certification status.
A CMMC Status is valid for three years from the CMMC Status Date for Level 3. Our team at Tech Dynamix helps organizations across Northeast Ohio carefully document their cybersecurity controls and prepare for the rigorous reporting requirements of both SPRS and eMASS, ensuring a smooth assessment process.
Frequently Asked Questions about CMMC
As CMMC continues its rollout, many questions arise, particularly regarding timelines, enforcement, and potential challenges. Here, we address some of the most common inquiries.
What are the timelines and future enforcement plans for CMMC 2.0?
The CMMC 2.0 program is currently in its rulemaking phase. While the proposed rule for the CMMC Program was issued on December 26, 2023, and the 48 CFR CMMC rule cleared regulatory review on August 25, 2025 (published September 10, 2025), CMMC will not be enforced on federal contracts until the final rulemaking has completed and been incorporated into both the 32 and 48 Code of Federal Regulations (CFR). This process is designed to provide clarity and legal standing for the program. Once finalized, CMMC requirements will be phased into DoD contracts, becoming a condition of contract award.
How does CMMC 2.0 impact contractors and subcontractors in the DIB?
The impact is significant and mandatory. If your business, operating anywhere from Lake County to the Greater Cleveland Area, handles FCI or CUI, you will need to achieve the specified CMMC level as a condition of contract award. This applies to both prime contractors and subcontractors. The program aims to create a consistent security baseline across the entire DIB supply chain, ensuring that sensitive information is protected at every link. This means proactive preparation is key for maintaining eligibility for DoD work.
Key Definitions within the CMMC Framework
Understanding the terminology is half the battle when it comes to CMMC. Let’s clarify some essential terms:
- Federal Contract Information (FCI): This is information, not intended for public release, that is provided by or generated for the Government under a contract. It does not include CUI. Level 1 of CMMC is designed to protect FCI.
- Controlled Unclassified Information (CUI): This is information that the Government creates or possesses, or that an entity creates or possesses for or on behalf of the Government, that a law, regulation, or Government-wide policy requires or permits an agency to handle using safeguarding or dissemination controls. This is the more sensitive type of unclassified information, and its handling triggers CMMC Level 2 or 3 requirements.
- Organization Seeking Assessment (OSA): This refers to any entity undergoing a CMMC assessment, whether it’s a self-assessment or a third-party audit.
- CMMC Third-Party Assessment Organization (C3PAO): An independent organization, accredited by The Cyber AB, authorized to conduct Level 2 CMMC certification assessments.
- Specialized Assets: These are assets that require specific security considerations within the CMMC framework. They include:
- IoT/IIoT (Internet of Things/Industrial Internet of Things): Connected devices that collect and exchange data.
- OT (Operational Technology): Hardware and software that monitor and control physical processes, devices, and infrastructure.
- Government Furnished Equipment (GFE): Equipment provided by the government to a contractor for use in fulfilling a contract.
- Restricted Information Systems: Systems with specific security restrictions.
- Test Equipment: Devices used for testing and validation that may contain sensitive data.
What are the main concerns regarding CMMC 2.0?
While CMMC 2.0 aims to streamline the program, several criticisms and concerns have been raised by industry professionals.
One significant concern revolves around the lack of centralized official communications from the DoD and The Cyber AB. This has sometimes led to confusion and uncertainty for contractors trying to prepare. Additionally, the accelerated timeline for rollout has been a point of contention, with many feeling that the deadlines are unrealistic, especially given the extensive changes required for compliance.
The sheer volume of assessments required for the vast Defense Industrial Base also presents a challenge. There are concerns that the number of accredited C3PAOs may not be sufficient to meet the demand, potentially creating bottlenecks and delays. This could particularly impact small and medium-sized businesses (SMBs) in Northeast Ohio, who might struggle with the costs and complexities of obtaining certification.
Past controversies within The Cyber AB, including leadership changes and concerns about a “Pay to Play” program, have also contributed to skepticism. While efforts are being made to establish trust, these historical issues highlight the need for transparency and clear governance.
Finally, while CMMC aims for reciprocity with other certification programs like FedRAMP, the guidelines are still a work in progress. Clearer guidance on how existing certifications might reduce the burden of CMMC compliance would be beneficial for many organizations. We understand these concerns and work to keep our clients informed of the latest developments and best practices.
Conclusion
The CMMC program is a transformative initiative designed to bolster the cybersecurity posture of the entire Defense Industrial Base. For businesses in Northeast Ohio, particularly those in the Greater Cleveland Area, Lake County, or Summit County, engaging with the DoD means embracing CMMC compliance as a fundamental operational requirement. It’s not just about passing an audit; it’s about building a robust and resilient cybersecurity framework that protects sensitive information, secures contracts, and contributes to national security.
At Tech Dynamix, we are deeply committed to helping our local businesses steer this complex landscape. With over 20 years of experience, we provide high-quality IT consulting and managed IT services, ensuring our clients have the proactive security measures and compliance readiness needed for CMMC. Our state-of-the-art ANSI/TIA-942 rated 4 datacenter and local expertise mean we’re well-equipped to guide you through the intricacies of CMMC Level 1, 2, or 3, from initial gap analysis to full assessment preparation.
Don’t let the complexities of CMMC deter you from pursuing valuable DoD contracts. We’re here to be your dependable, all-in-one technology partner, simplifying the process and strengthening your cybersecurity defenses.
Get started with Compliance & Security Audits today and ensure your business is ready for the future of defense contracting.