Why AI Network Security Matters for Modern Businesses
AI network security uses artificial intelligence and machine learning to detect, prevent, and respond to cyber threats faster and more accurately than traditional methods. Here’s what you need to know:
- What it does: Monitors network traffic, learns normal behavior patterns, and identifies suspicious activity in real-time
- Key difference: Unlike signature-based systems that only catch known threats, AI can help detect zero-day attacks and novel intrusions
- Core technologies: Machine learning, deep learning, behavioral analytics, and automated response systems
- Main benefits: Faster threat detection, reduced false positives, proactive defense, and 24/7 automated monitoring
Cyber threats are evolving at a pace that traditional security tools simply can’t match. Signature-based defenses, the kind that rely on databases of known attack patterns, struggle with new and sophisticated intrusions. That can leave organizations vulnerable to zero-day attacks, advanced persistent threats, and polymorphic malware that changes to evade detection.
AI network security changes the game by learning what normal network behavior looks like, then flagging anything that deviates from that baseline. Instead of waiting for a threat signature to be added to a database, AI-powered systems analyze large amounts of data in real-time, spot anomalies, and respond automatically, often before human analysts even see the alert.
This isn’t just theoretical. Organizations using AI-driven security solutions often report improved threat detection accuracy while reducing the flood of false positives that can overwhelm security teams. AI systems can process complex data structures using multilayer neural networks, analyze user and entity behavior to catch insider threats, and help predict potential attack scenarios based on historical patterns.
I’m Jay Baruffa, and over the past 20 years in IT infrastructure design and cybersecurity, I’ve watched ai network security transform from research labs into practical tools that protect Northeast Ohio businesses every day. At Tech Dynamix, we help companies implement these intelligent defenses without the complexity or cost of managing them in-house.
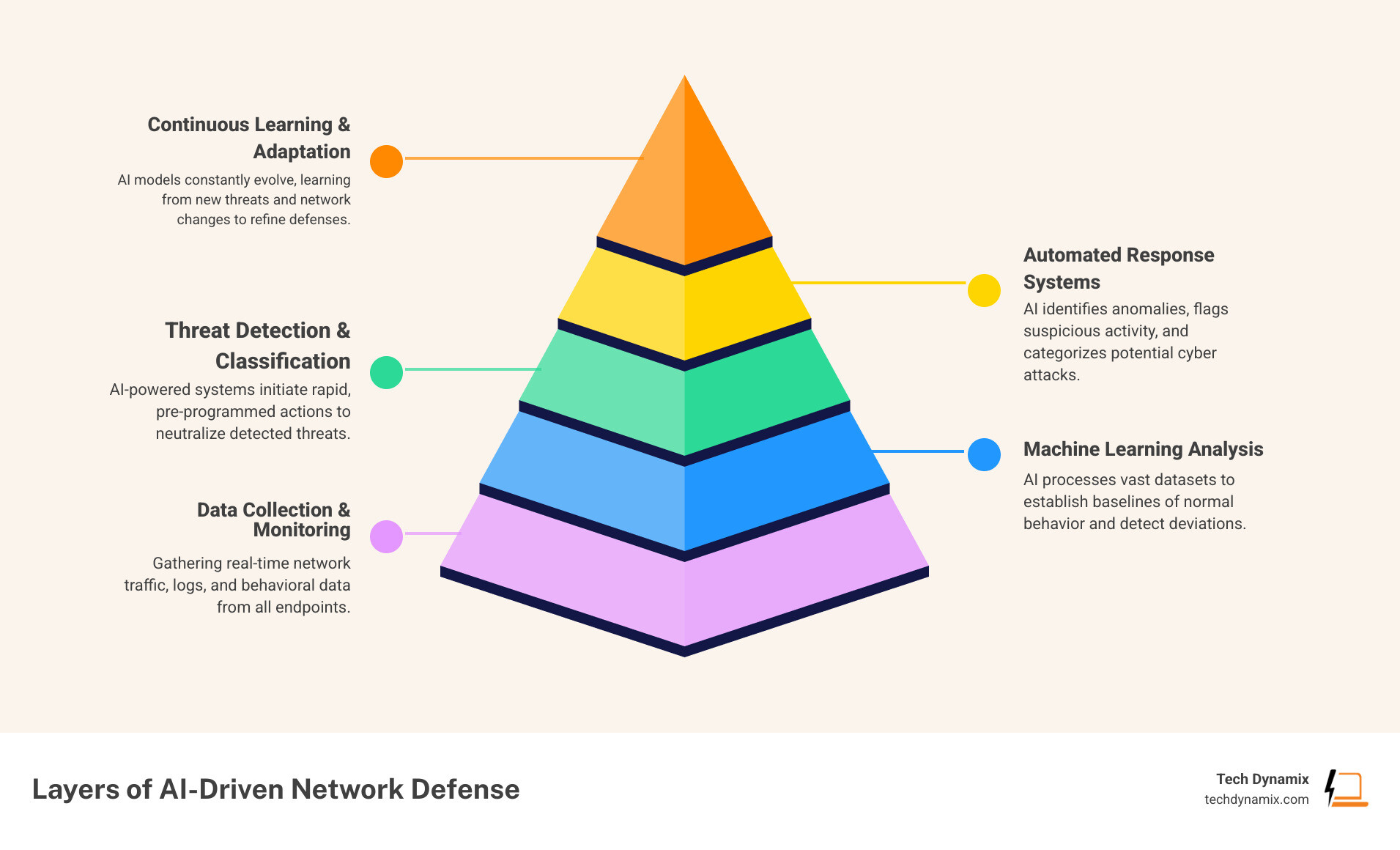
Understanding AI Network Security: Beyond Traditional Defenses
AI network security represents a paradigm shift from reactive measures to intelligent, predictive defense. It leverages artificial intelligence to protect networks against everything from common malware to sophisticated advanced persistent threats.
The fundamental difference lies in methodology. Traditional security relies on signature-based detection—checking IDs against a blacklist. While effective for known threats, it fails against zero-day exploits that lack a pre-existing signature.
AI network security uses machine learning and deep learning to establish a baseline of “normal” behavior. By analyzing network traffic, user activities, and application usage, it identifies deviations as anomalies in real-time. This reduces the window between threat identification and response.
| Feature | Traditional Network Security | AI Network Security |
|---|---|---|
| Detection Method | Signature-based, rule-based | Anomaly detection, behavioral analysis |
| Threat Coverage | Known threats | Known, unknown, and zero-day threats |
| Adaptability | Low, requires manual updates | High, continuous learning |
| Response Time | Delayed, often manual | Real-time, often automated |
| Data Analysis | Limited, manual log analysis | Massive scale, high-speed processing |
| Proactive Posture | Reactive | Proactive, predictive intelligence |
AI systems process complex data using multilayer neural networks to identify subtle patterns. For technical details, see artificial intelligence and machine learning in cybersecurity: a deep dive. At Tech Dynamix, we translate these complexities into cybersecurity solutions for Northeast Ohio businesses.
The Evolution of AI Network Security
Security AI has evolved from 1980s-era heuristic analysis (rule-based logic) to modern machine learning (ML) and deep learning (DL). Unlike static models, ML algorithms learn from data patterns. Deep learning uses layered neural networks to recognize complex, polymorphic threats that change their code to evade detection. This continuous adaptation allows AI to improve over time, reducing false positives and staying ahead of evolving malware.
Proactive vs. Reactive Security Postures
AI shifts security from reactive to proactive through:
- Predictive Intelligence: AI correlates data from multiple sources to create threat profiles and identify vulnerabilities—like outdated OS or unprotected data—before they are exploited.
- Threat Hunting: AI sifts through massive datasets to uncover subtle indicators of compromise that human analysts might miss.
- Incident Prevention: By spotting anomalies early, AI allows for intervention before an attack materializes.
- Scalability: AI automates triage and data analysis, allowing security professionals to focus on strategic initiatives rather than manual log review.
How AI Improves Threat Detection and Response
AI acts as a tireless guardian, spotting anomalies and reacting with speed.
Techniques like User and Entity Behavior Analytics (UEBA) learn “normal” behavior for every device and user. If an employee suddenly downloads massive volumes of data from an unusual location at 3 AM, AI flags it as a potential insider threat or breach. AI also improves Intrusion Detection Systems (IDS) by identifying patterns in traffic rather than just matching signatures.
AI helps identify all network endpoints, ensuring they are managed and updated. You can learn more about AI threat detection capabilities. For local businesses, this often begins with a compliance and security audit to identify current gaps.
Predictive Intelligence in AI Network Security
AI forecasts threats before they strike by:
- Threat Profiles: Correlating data across the organization to build dynamic profiles of potential attackers.
- Indicators of Compromise (IoCs): Rapidly cross-referencing malicious IPs, domains, and file hashes across the network.
- Contextual Analysis: Enriching data with global threat feeds to differentiate between benign glitches and genuine attacks, reducing false positives.
- Early Warning: Predicting attack vectors based on historical trends and current vulnerabilities.
Automating Incident Response and Mitigation
AI reduces “dwell time”—the time an attacker spends in your network—through automation:
- Automated Actions: AI can instantly isolate affected systems, block malicious IPs, or force MFA resets to contain a threat.
- Malware Neutralization: AI flags suspicious encryption patterns early, helping to stop ransomware before it spreads.
- Reduced Workload: Automating routine responses frees human experts for complex problem-solving and reduces the risk of human error.
- Workflow Optimization: AI prioritizes alerts and translates complex data into natural language, helping junior analysts respond more effectively.
Industry Use Cases and the Role of Generative AI
AI network security adapts to the specific needs of different sectors across Northeast Ohio:
- Healthcare: AI protects patient records by detecting unusual access patterns and blocking ransomware before it can disrupt hospital operations.
- Financial Services: AI analyzes transaction patterns to identify and block fraud in real-time.
- Education: AI monitors campus networks for unauthorized access to records and manages access to restricted research.
- Enterprise & Infrastructure: AI detects insider threats and protects critical infrastructure from large-scale disruptions.
CISA explores these tools to strengthen national cybersecurity. See CISA Artificial Intelligence Use Cases for more.
Implementing Generative AI for Network Security
Generative AI adds new capabilities to the security toolkit:
- Synthetic Data: Creating realistic data to train ML models without exposing sensitive real-world information.
- Attack Simulations: Generating realistic scenarios to test defenses and train security teams.
- Natural Language Insights: Allowing analysts to query complex data using plain English and receive step-by-step mitigation instructions.
Microsoft provides further strategies for using generative AI-powered security.
AI in Identity and Access Management (IAM)
- Biometric Authentication: AI improves the accuracy of facial and fingerprint recognition to prevent brute-force attacks.
- Adaptive MFA: AI triggers extra authentication steps only when a login attempt appears risky (e.g., unusual location or device).
- Credential Stuffing Prevention: AI recognizes patterns of automated login attempts using stolen credentials.
- Privilege Monitoring: AI flags unusual privilege escalation, helping catch compromised accounts.
Tech Dynamix managed services integrate these IAM solutions to provide secure, user-friendly access control.
Navigating Challenges and Implementation Best Practices
Implementing AI requires addressing specific risks. Data quality is paramount; biased or incomplete training data leads to unreliable predictions. Privacy concerns also arise, requiring strict adherence to data governance standards like the Directive on Automated Decision-Making.
Adversarial machine learning is a growing threat where attackers manipulate data to fool AI. This includes data poisoning (corrupting training sets) and adversarial examples (modifying malware to look benign). Additionally, the “black box” nature of some AI makes it difficult to understand why certain decisions were made.
Required Skills for AI Security Professionals
Effective AI security management requires a blend of skills:
- AI/ML Knowledge: Understanding algorithms and neural networks.
- Cybersecurity Expertise: Foundations in networking, forensics, and cryptography.
- Data Science: Proficiency in managing and interpreting large datasets.
- Ethics & Law: Understanding privacy regulations like GDPR and CCPA.
Best Practices for a Secure AI Integration
- Strategic Roadmap: Identify high-impact areas for AI before deployment.
- Data Governance: Ensure training data is accurate, diverse, and secure.
- Seamless Integration: Ensure AI tools complement existing infrastructure without creating bottlenecks.
- Continuous Learning: Regularly update models with new threat intelligence to counter adversarial attacks.
- Transparency: Maintain ethical standards and clear policies for AI usage, especially regarding sensitive data.
By following these steps, Northeast Ohio businesses can build resilient, intelligent defenses.
Frequently Asked Questions about AI Network Security
Will AI replace human cybersecurity professionals?
No. AI augments human expertise. It handles the heavy lifting of data processing and repetitive tasks, freeing professionals to focus on strategic decision-making and complex investigations. The future is a partnership where AI provides the speed and humans provide the context.
What are the primary risks of using AI in network security?
- False Positives: Benign activity may be flagged, causing alert fatigue.
- Data Bias: Incomplete data can lead to ineffective security decisions.
- Adversarial Attacks: Attackers may manipulate data to bypass AI defenses.
- Skills Gap: Specialized expertise is required to manage these systems.
- Privacy: Extensive data analysis requires robust governance.
How does AI help minimize the impact of ransomware?
- Early Detection: AI identifies unusual encryption patterns or communication with malicious servers.
- Automated Isolation: AI can instantly disconnect infected devices to prevent lateral spread.
- Encryption Prevention: Rapid response can stop the encryption process before critical data is lost.
- Faster Recovery: AI provides insights into the attack’s scope, accelerating the restoration process.
This proactive approach is essential for protecting organizations across Northeast Ohio from modern ransomware threats.
Conclusion: The Future of Digital Resilience
The landscape of cyber threats is constantly evolving, growing more sophisticated and pervasive with each passing day. In this dynamic environment, traditional network security approaches are simply no longer sufficient. AI network security represents the essential leap forward, offering unparalleled capabilities in threat detection, response, and proactive defense. By leveraging machine learning, deep learning, and behavioral analytics, AI empowers organizations to move beyond reactive measures, embracing a future where digital fortresses are built with intelligence and adaptability.
For businesses in Northeast Ohio, from Painesville to Cleveland, and throughout Lake County and Summit County, embracing AI network security isn’t just about adopting new technology; it’s about securing your future. It means protecting your data, your operations, and your reputation against an increasingly complex array of cyber adversaries. While challenges like data quality, adversarial attacks, and the skills gap exist, strategic implementation, adherence to best practices, and a commitment to continuous learning can overcome them.
At Tech Dynamix, we understand these complexities. With over 20 years of experience providing high-quality IT consulting and managed IT services to small and mid-size businesses across Northeast Ohio, we are your dependable all-in-one technology partner. We specialize in translating advanced concepts like AI network security into practical, effective solutions that work for you. Our proactive IT support, cybersecurity protection, and expert guidance ensure that your business is not just reacting to threats, but anticipating and neutralizing them.
Don’t let evolving cyber threats leave your business vulnerable. Partner with us to open up the full potential of AI network security and build a resilient digital future.
Secure your business with Tech Dynamix cybersecurity solutions



